How using ssh tunneling in Database Tools might leak your connection forever
Recently, while developing TablePlus, we researched about SSH tunneling technology. After testing several database tools which supported ssh tunneling, we discovered that your connection might be leaked until you disconnected from the internet or shut down your machine. The leak is caused by using open-ssh to create a tunneling. So what is ssh tunneling? And why do we need it to connect to a remote database? Please see the diagram below.
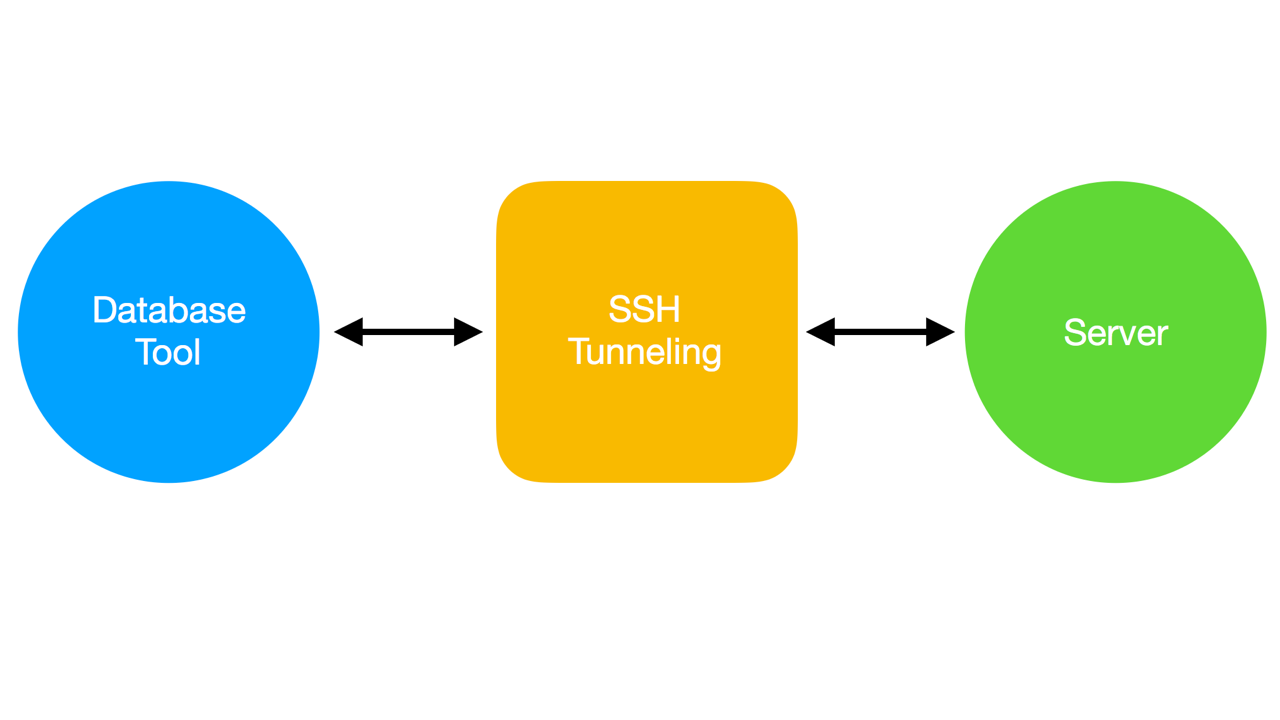
Because of security reasons, almost every host does not allow clients to connect directly to the database from outside of the server. That’s why database tools need to create a tunneling. The tunneling works as a middleware that transfers data between client and server over ssh. It is encrypted by public/private keys and it’s safe.
However, building an ssh lib demands time and neat programming. Many tools out there are using open-ssh to create a tunneling. The problem is that open-ssh process is not managed by the application. Therefore, sometimes even when the application is closed (crashed), the tunneling still exists. This is really dangerous because users aren’t aware of that. Things might get worse as other applications can use the tunneling without app permission because it was created outside of the app.
So how dangerous is it? Of course, the connection is still on your machine, and you need to know the server password to connect to the database. However, sometimes the server was configured with an option to accept connection by peer without a password. Or a malware on your computer might just brute force the password. Think about that.
Let me reproduce the issue. Try these steps on your database and you will get what I’m saying.
Step 1: Use ssh feature in PSEquel or SequelPro to create a tunneling to connect to the server.
Step 2: Open terminal and type "ps aux | grep ssh". You will see the tunneling like “/usr/bin/ssh root@<the server ip> -vNL 58070:localhost:5432 -p 22 -o ExitOnForwardFailure=yes -o ConnectTimeout=30 -o TCPKeepAlive=no -o ServerAliveInterval=60”
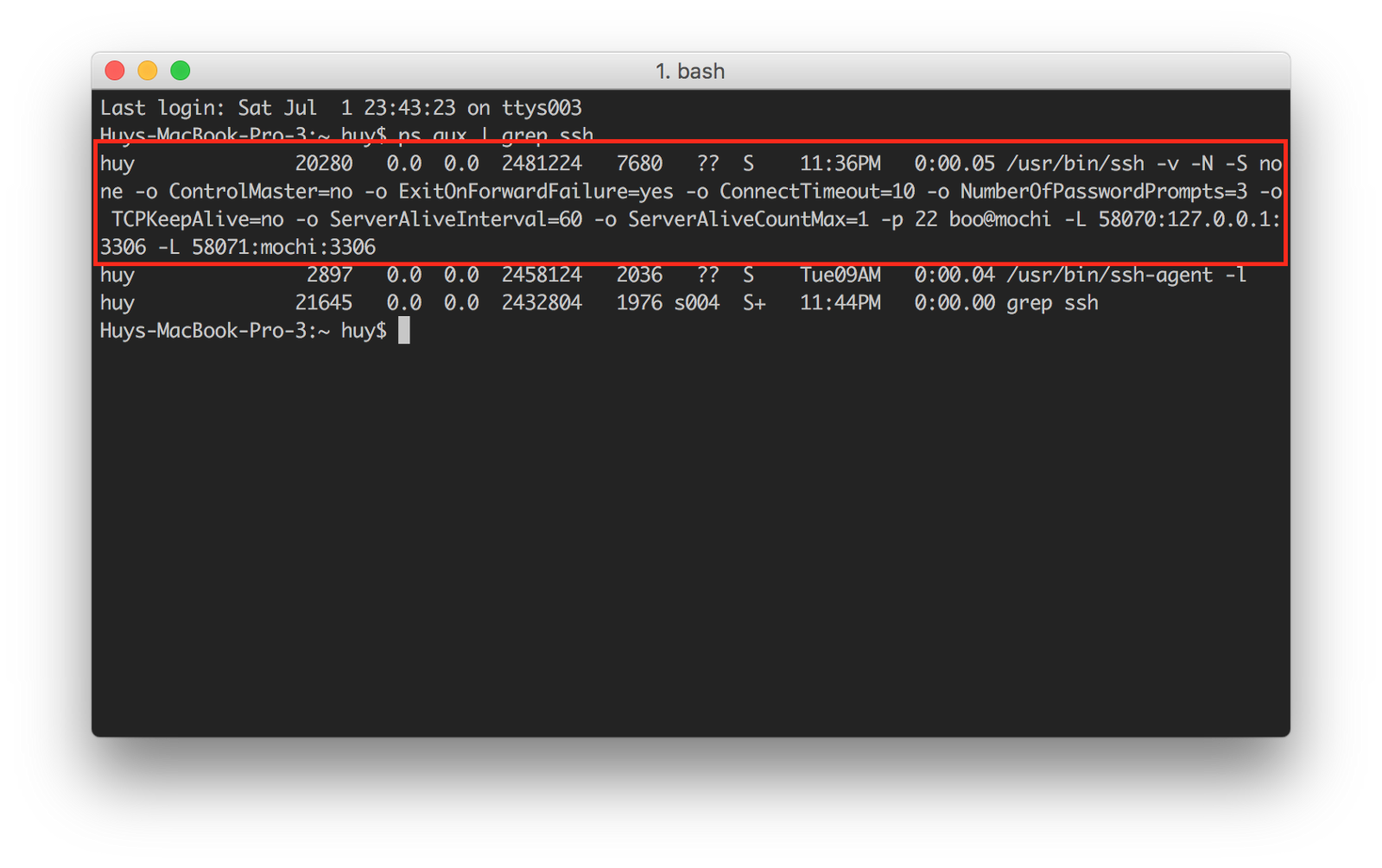
Step 3: Force quit the app (using command + option + esc).
Step 4: Type "ps aux | grep ssh" again and you can see the ssh still exists.
Let’s connect to the server using the tunneling:
Open TablePlus and input the server info. Enter the port being showed in ssh tunneling. In my case, it is 58070 (enter the password if needed).
Hit the connect button, and the connection will be made. You can see the ssh still exists unless you kill it or the internet are disconnected.
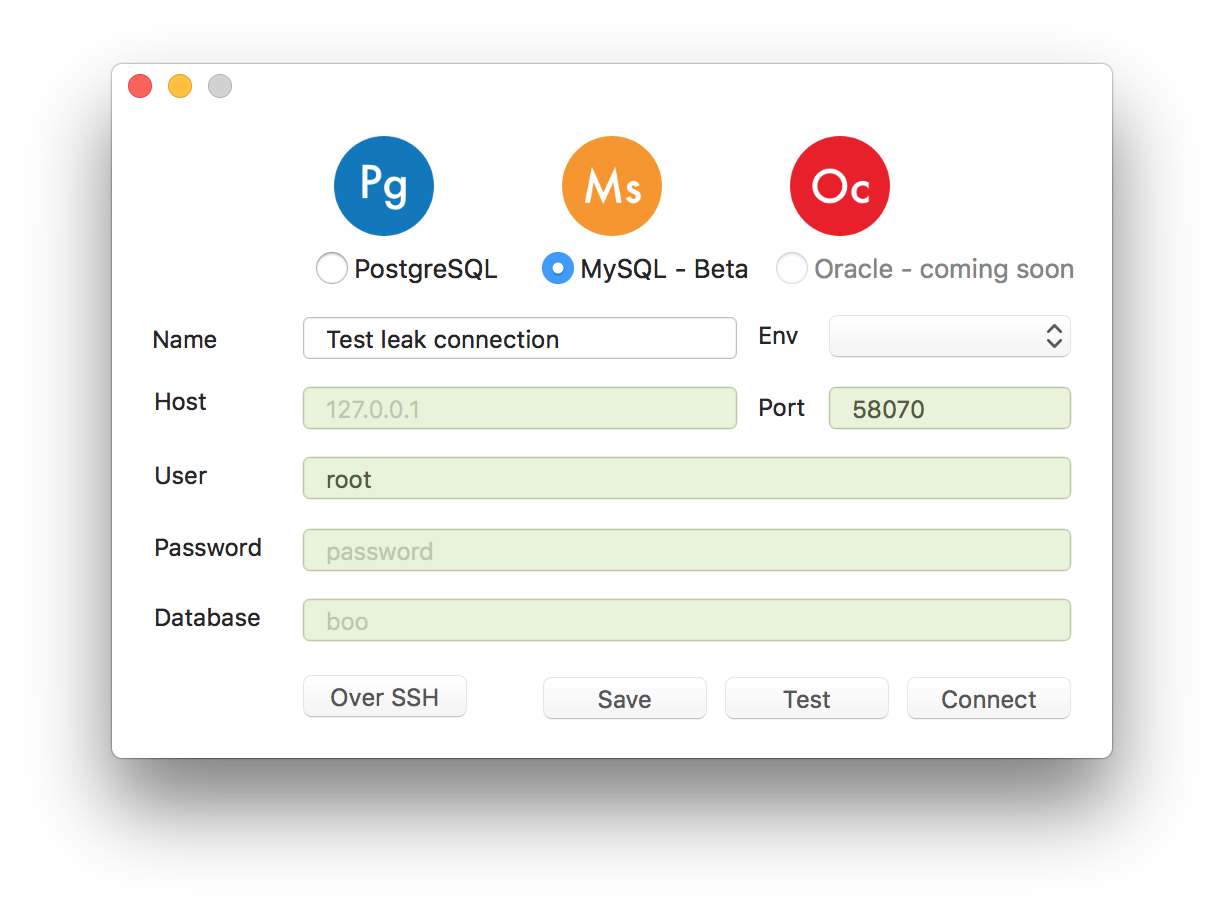
So how do I know if a tool is using open-ssh? Simply type ps aux | grep ssh when you are using a database tool and connecting to the server with ssh mode.
Being aware of that, TablePlus has implemented its own ssh lib with https://libssh.org and secured the port. That’s why you can’t see the ssh tunneling in the terminal. Because ssh tunneling is a part of TablePlus, the application can control the number of connections through ssh. TablePlus only accepts connections from itself and prohibits connections from the outside. That’s how you can secure your connection and protect your database.