Why is using Native SSH Tunnel important to secure your database?
What is SSH?
Secure Socket Shell or SSH is a network protocol which provides a secure channel between a local and remote computer using a Server-Client model. It’s generally used to securely operate remote shell service and file transfer over an unsecured network.
SSH is actually a suite of three utilities - slogin, ssh, and scp - that are secure versions of the earlier UNIX utilities: rlogin, rsh, and rcp. SSH commands are encrypted and protected via several types of authentication, including password, keyboard-interactive, public-key, or none. Public-key authentication is a very secure authentication method and it is recommended over the password-based authentication which can be cracked with a brute force attack.
How SSH Tunneling works?
To create an SSH tunnel, you need:
Database Serverwhere your data is being stored.SSH Serverlistening for connections from the client.SSH Clientconfigured to forward traffic from a local listening port, through the SSH server, to the Database Server.
When the SSH Client initiates a connection to the Database Server, it has to negotiate with the SSH Server first. They will try to reach an agreement on which authentication method is being used that both support. Let’s say they use public-key authentication, then a secure handshake will begin validating against the key pair. Once the SSH Server can verify that the private key hold by SSH Client matches with its public key, the system is unlocked and a secure connection is established between the SSH Client and the SSH Server. We call it SSH Tunnel.
The SSH Server will need to have access to the listening port on the Database Server and acts as a middleware transferring data between the client and database server securely.
That way, your data connection is safe.
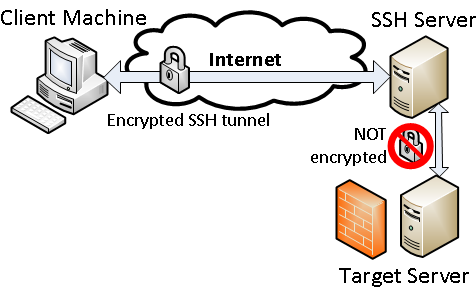
The network between the SSH server and the Database Server are NOT encrypted by the SSH Tunnel, so if these two servers are running on different machines, they should be communicating over a secure network for optimum security.
Why should you use SSH Tunneling?
It’s considered best practice to not have your production database servers accessible via any public channels. This means that you should build an SSH tunnel as an extra layer of protection. The public-key cryptography used by SSH protocol for authentication is an industry standard and it’s pretty easy to install.
But, there are still problems…
Most database clients can be able to create an SSH Tunnel. The thing is, building an SSH lib requires time and neat programming. So most of them ended up using open-ssh to create a tunnel which might leak connection data. That topic is clearly demonstrated in this post.
Being aware of that, TablePlus has implemented its own SSH lib with https://libssh.org and secured the port. Because SSH Tunneling is a part of TablePlus, the application can control the number of connections through SSH. TablePlus only accepts connections from itself and prohibits connections from the outside. That’s how you can secure your connection and protect your database.
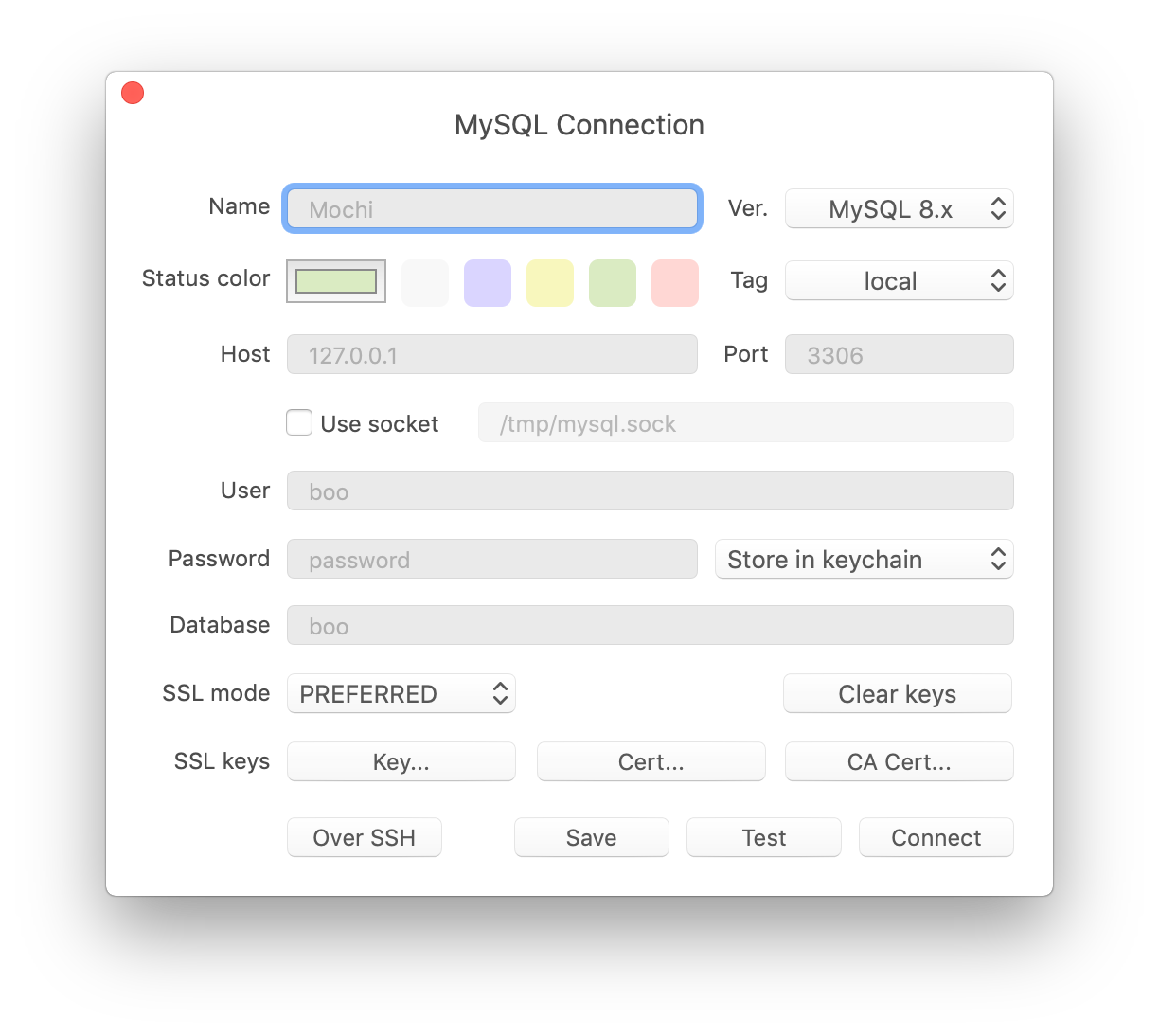
TablePlus is a modern, native tool with an elegant UI that allows you to simultaneously manage multiple databases such as MySQL, PostgreSQL, SQLite, Microsoft SQL Server and more.
Not on Mac? Download TablePlus for Windows.
On Linux? Download TablePlus for Linux
Need a quick edit on the go? Download TablePlus for iOS.