Best practices to keep your production database secure
Security is always a top priority in database management as database contains valuable information of the business and it has never been more attractive in the eyes of the hackers. But when an application communicates data over a public network, it always shows a sense of vulnerability. Adding some extra security layers is critical to preventing exposure to malicious attacks and ensuring the continued security of your database.
Below are some of the best practices that we encourage to protect your database when accessing it over a public network.
1. Always use native SSH
It’s considered best practice to build an SSH tunnel to transfer data between your client and the database server as an extra layer of protection. The public-key cryptography used by SSH protocol for authentication is an industry standard and it’s pretty easy to install. Most database clients have the built-in capability to define an SSH tunnel to connect to a database, but it might not be 100% secure.
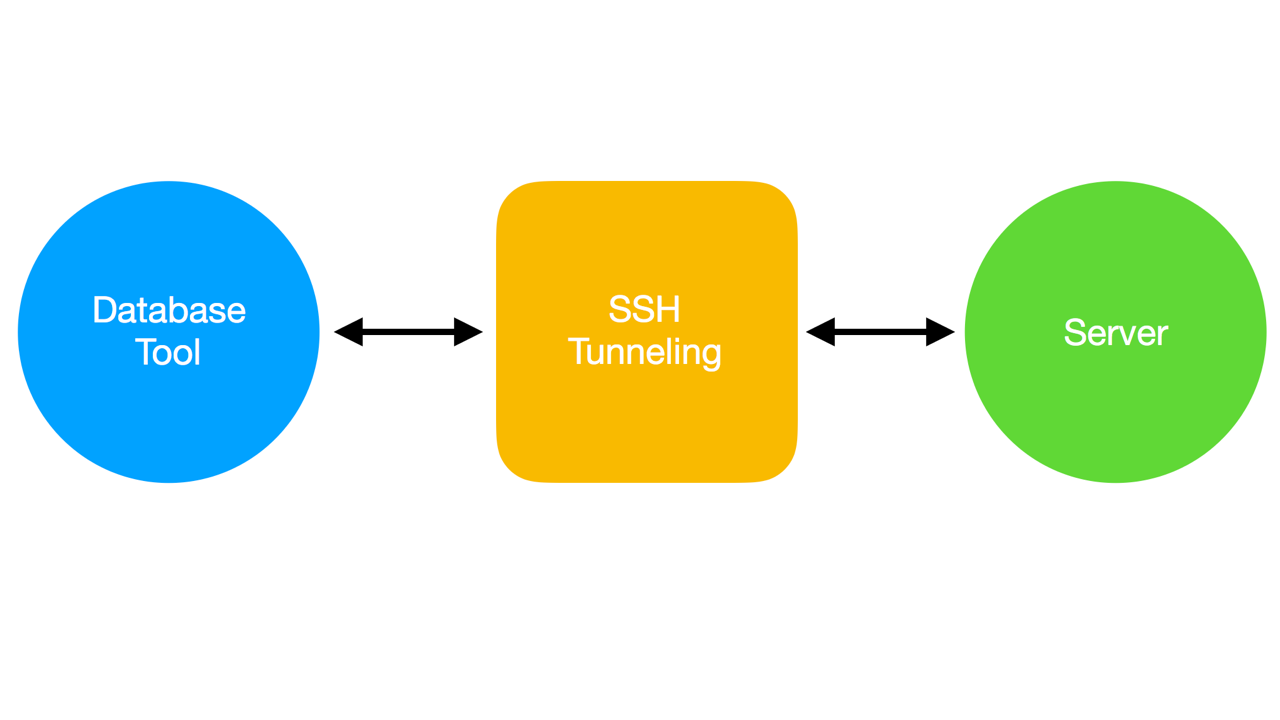
Read more on why you should use native SSH and why using database tool might leak your database connection.
2. Always use SSL
To keep information safe, it’s standard procedure to encrypt stored data, but it’s also important to encrypt all connections to it for protecting the authentication credentials from interception. SSL will help you with two main functions:
- To prevent the data from being seen/altered by the attacker listening on the network.
- To ensure that the client is connecting to the authentic server, and not a man-in-the-middle.
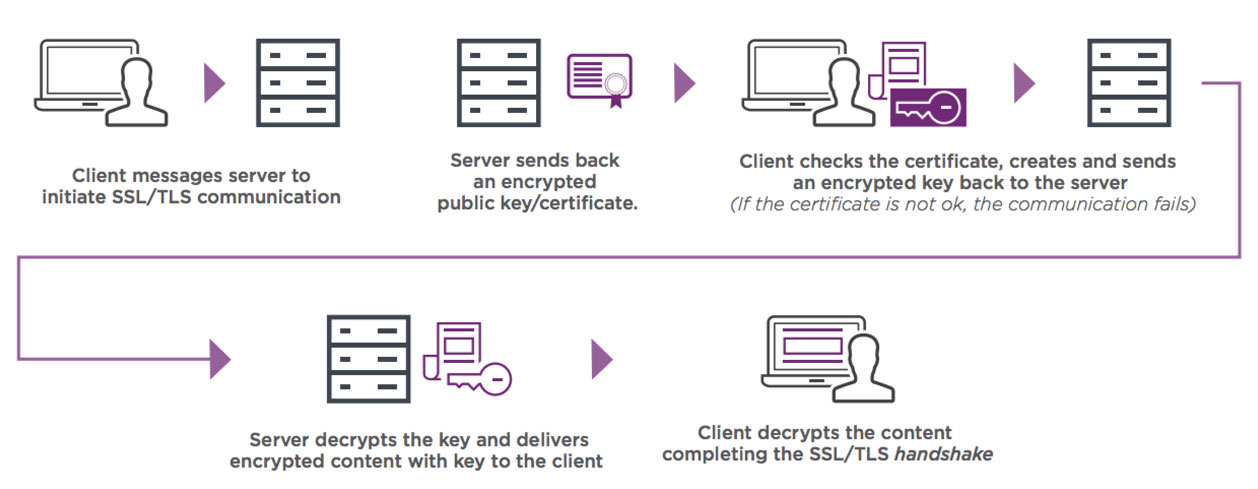
Read more on why you must always use SSL on production.
3. Use two-factor authentication
You should enable multi-factor SSH authentication to protect your SSH Server and make double sure that no one else can access to your database. A common implementation is an OATH-TOTP app, like Google Authenticator, makes Multi Factor Authentication easy to integrate and use. Logging into your server via SSH will then requires two factors across two channels, thereby making it more secure than a password or SSH key alone.
Read more on two-factor authentication and keyboard-interactive.
4. Prevent SQL Injection Attacks
SQL Injection is a code injection attack where hackers can insert and execute malicious SQL statements that give them the control of a web app database server. It’s the most common technique used in exploiting web application vulnerability. It’s very easy to perform and once the attackers manage to break in, it’s going to be a catastrophe.
It’s best to be cautious and implement some prevention methods to keep your databases secure from SQL Injection Attacks such as validate and sanitize all user input, avoid using dynamic SQL and use stored procedures instead.
Read more on What is SQL Injection and 8 best practices to prevent SQL Injection Attacks.
5. Beware of pirated or cracked applications
Using a cracked app, you are taking some risks that lead to undesired outcomes such as:
- Hackers might inject some malicious code into the app that will slow your computer down, send out your sensitive information, damage your files…
- The app might stop working and you can’t get support.
- It’s illegal and you can get into trouble.
- The development might be abandoned due to lack of financial support.
Read more on why you should never use cracked apps.
TablePlus is a modern, native tool with an elegant UI that allows you to simultaneously manage multiple databases such as MySQL, PostgreSQL, SQLite, Microsoft SQL Server and more.